What is a Whitelist?
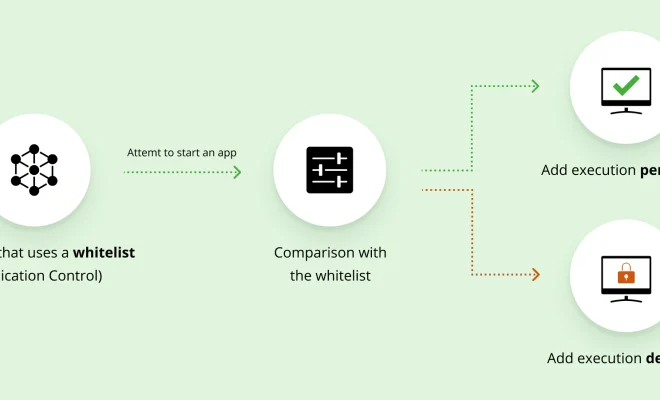
A whitelist is a powerful tool that is commonly used in online security and privacy management. It is a list of approved or trusted websites, software, IP addresses or email addresses that can be accessed, connected to or interact with a particular system, application or network. In other words, it is a protection mechanism used to limit access to only those that are deemed safe or desirable.
Whitelisting is often the preferred security option for organizations as it allows for tighter control over the devices, applications and software that are allowed to connect to their systems. Since only trusted and approved resources are allowed to interact with the network or device, this significantly reduces the risk of breaches, malware or viruses being introduced to the system. It also helps to prevent unauthorized or malicious activities, like phishing emails or hacking attempts.
Whitelisting is used in a variety of contexts, including firewalls, email filtering, and software applications. For example, a company might use whitelisting to limit access from specific IP addresses, block certain websites or social media platforms, or only allow connections from specific software vendors. This helps to prevent employees from accessing or using unauthorized resources, potentially compromising company data, or becoming subject to phishing scams.
Another use of whitelisting is for software applications. This is particularly important for organizations that rely on third-party software for business operations. By creating a whitelist of approved software, they can minimize the risk of downloading malicious software or applications that could harm their systems. This also helps to ensure compliance with data security standards and regulations.
While a whitelist is an essential part of any security strategy, it is important to keep it updated and maintained regularly. As new threats and vulnerabilities are discovered, it may be necessary to update or modify the whitelist accordingly. Additionally, new technologies and applications may need to be reviewed and approved before being added to the whitelist.






