What Is a Hidden File?
A hidden file is a file that is intentionally set to be hidden from the user. Hidden files are typically used by computer and software developers to store information that is not necessary for the user to see or manipulate. These hidden files can vary in size and type and can be found on any computer system, regardless of the operating system being used.
There are several reasons why developers set files to be hidden. For one, hidden files can contain important system files, which if deleted or modified, can cause serious issues with the proper functioning of the computer. Additionally, developers may also use hidden files as a way to store configuration data or settings that are used by a program or an application.
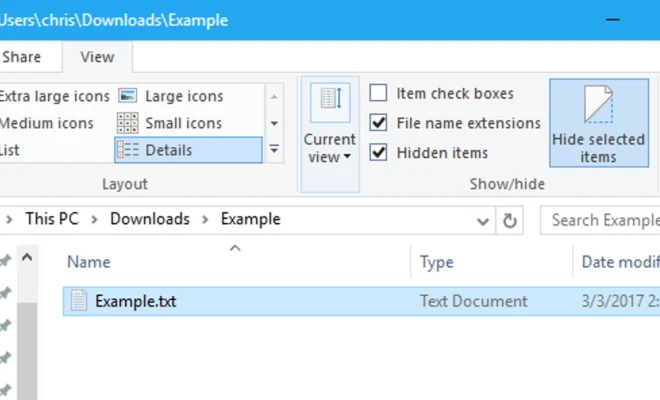
It is important to note that while hidden files are not displayed in regular file managers, they can still be accessed and manipulated by users with the appropriate permissions. For example, a user with administrator-level permissions can show hidden files in Windows by going to the Folder Options menu in the Windows Explorer and selecting the ‘Show hidden files, folders and drives’ option.
Hidden files can serve both good and bad purposes. Unfortunately, hidden files can be used by malware and viruses to evade detection by antivirus software. Cybercriminals may also use hidden files to spread malicious software, steal sensitive information or gain access to a computer network.
As hidden files can be used for both good and bad purposes, it is important for users to ensure that they understand how to manage and access them. By showing hidden files when necessary and appropriately configuring file permissions, users can maintain a secure and efficient computing environment.
In conclusion, hidden files are an important aspect of computer and software development. They can be used to store important system files or configuration data, but users need to be mindful of their existence and significance. While hidden files can be accessed and manipulated by authorized users, cybercriminals are known to use hidden files to gain access to sensitive information, making it essential for users to maintain a secure computing environment.