What is a default in information technology?
A default in information technology (IT) refers to a pre-set configuration or setting that a system or software program will revert to if no changes are made. In other words, it is the standard state of a system or software before any changes are made
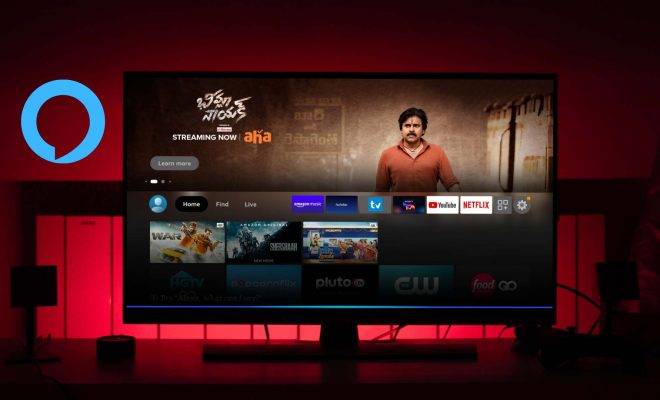
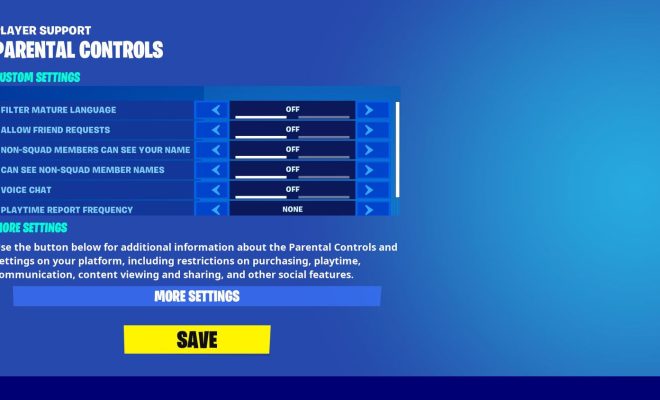
In IT, defaults can be found in a variety of areas, including software configuration, operating system settings, networking protocols, and security parameters. For example, web browsers come with default settings, such as homepage and search engine preferences. Likewise, a network router comes with default settings for IP addresses, username and password, and network security
Defaults play a crucial role in managing IT systems, as they help ensure consistent and predictable behavior across different devices and platforms. They also save time and effort by allowing users to quickly and easily configure and initialize systems without the need for extensive setup and configuration. Defaults can also provide a baseline of functionality and security to prevent unauthorized access or changes to the system
However, defaults can also pose certain risks, particularly in terms of security. Hackers and cybercriminals often exploit known default settings to gain unauthorized access to systems or networks. This can result in data breaches, network disruptions, and other cyber threats that can cause significant damage to organizations
To mitigate these risks, IT professionals need to be aware of the default settings in their systems and make appropriate adjustments to enhance security. This may involve changing default passwords, disabling unnecessary services, or implementing additional security measures such as firewalls, encryption, or two-factor authentication
In conclusion, defaults are an essential aspect of information technology that provide a baseline of functionality, consistency, and predictability. However, they can also pose security risks if not properly managed or secured. To maintain robust and secure IT systems, organizations need to be aware of the default settings in their technologies and take appropriate measures to reduce vulnerabilities and prevent cyber threats.